All the opinions youll read here are solely ours, Find out more about MDR from Cybriant: https://cybriant.com/mdr/, There are at least 5.8 billion enterprise endpoints in use in 2020 Source, 68% of organizations were victims of endpoint attacks in 2019 Source, 91% of cyberattacks start with a phish, and the top reasons people are duped by phishing emails are curiosity (13.7%), fear (13.4%), and urgency (13.2%), followed by reward/recognition, social, entertainment, and opportunity. This type of malware can cripple entire systems or even render them useless. The cybersecurity market is growing at a fast pace.
endpoint By using enterprise endpoint security solutions, you can use field-proven AI to inspect any application attempting to execute on an endpoint before it executes. Something that differentiates cybercrime from any other kind of crime is the automation that can be deployed by perpetrators. The same report found that 68% of IT professionals found that the frequency of endpoint attacks had increased since the year before. As an Amazon Associate we earn commissions from qualified purchases. Malware statistics point to an astronomical increase. Perhaps the more concerning side to cyber security statistics, in general, is the number of incidents that have gone unreported. Did you know that most people would plug an unknown flash drive into their computer? With the increase of endpoints like laptops, smartphones, tablets, and other mobile devices, so the risk of losing data is also increasing day by day. Memory-based attacks are on the rise as attackers realize the ease with which memory can be exploited to achieve their goals. Alpharetta, GA 30022 based on our tests and personal experience with a product/service. If these cyber security statistics for 2022 werent enough for you, rest assured theres many more below. System upgrades are not the easiest thing to implement. Google Drive, Amazon S3 and Mega.nz are the most common cloud storage services for storing exfiltrated data. Weve put together a series of guides to the top solutions that will defend your endpoints against viruses, malware and malicious applications, and help you mitigate the consequences of ransomware attacks: The Top 11 Endpoint Security Solutions For Business, The Top 10 Antivirus Software For Small Businesses, The Top Unified Endpoint Management (UEM) Solutions, The Top 10 Office 365 Backup And Recovery Solutions, 50 Endpoint Security Stats You Should Know In 2022, 81% of businesses experienced some sort of malware attack (Ponemon), public sector organizations are less likely to be affected, the cost of a successful endpoint attack has increased, Lack of physical security in the workspace (47%), Criminals gaining control over remote devices to steal sensitive data (24%), Criminals leveraging devices to gain network access (17%), Phishing and social engineering attacks (15%), Securing external access to internal resources (8%). Statista assumes no In turn, security teams will need to utilize ML defensively to protect network and information assets as well as to enhance enterprise security solutions. Examples of Ransomware: 7 Cyber Security Trends To Fight Back. Can Traditional Enterprise Antivirus Protect from Unknown Threats? Often it is data breaches that steal the headlines. Please do not hesitate to contact me. Todays enterprise security solutions do not require any previous knowledge about a malicious binary file to identify its intention. They can also include measures to protect against ransomware and other types of malware. A portion of the rise is a result of the increased number of IoT devices, but the more significant issue is that related security isnt keeping pace with the growing number of threats. On average, 80% of successful breaches are new or unknown zero-day attacks.

Once downloaded to the victims device, the malware holds corporate data hostage by locking users out of it or encrypting it until the target organization pays a ransom.

Smaller companies are more prone to cyber-attacks because they dont employ proper defenses against advanced cyber threats, contributing heavily to these cyber security statistics. Threat actors are creating malware like crazy. They can also help to prevent malicious software from infecting your devices. This, coupled with the projections for further data breaches, spells future challenges. Cyber attack statistics show this to be a key reason why harmful software for mobile devices is not such an issue anymore. These measures can include antivirus software, firewalls, and spam filters. By the end of 2021, there were, The Best Money Making Apps You'll Find in 2022 (Tested & Reviewed), 10 Best Appointment Scheduling Software for 2022, 11 Top CRM Software For Your Business for 2022, 10 Best Project Management Software for 2022, 10 Best Web Conferencing Software for 2022, 11 Best Membership Management Software for 2022, 9 Best Data Visualization Software for 2022, 10 Best Document Management Software For A Paperless Office for 2022, 12 Best Event Management Software for 2022, 11 Best Digital Signature Software for 2022, 10 Best Customer Experience Management Software for 2022, 10 Best Payment Gateway Providers for 2022, 20 Best Lead Generation Software For Marketers for 2022, 10 Best Reputation Management Software for 2022, 10 Top Contact Management Software for 2022, 14 Best Facebook Chatbots For Your Business Website for 2022, 10 Best Email Marketing Services for 2022, 9 Best Social Media Management Tools for 2022, 5 Leading Tax Software Solutions for 2022, 10 Best Online Bookkeeping Services for 2022, 10 Best Expense Management Software for 2022, 6 Best Web Hosting Companies In India for 2022, 9 Best WordPress Hosting Companies for 2022, 12 Best Privacy Policy Generators for 2022, 9 Best WordPress Security Plugins for 2022, 10 Best Minecraft Server Hosting Providers for 2022, 10 Best Shared Hosting Providers for 2022, 10 Best Cheap VPS Hosting Providers for 2022, 10 Best HR Software For Successful Business Leaders in 2022, 10 Best Employee Monitoring Software for 2022, 10 Best Employee Engagement Software for 2022, 10 Best Medical Billing Software for 2022, 10 Excellent Property Management Software for 2022, 16 Best Audio Recording Software for 2022, 11 Best Inventory Management Software for 2022, 10 Best Field Service Management Software for 2022, 10 Best Network Monitoring Software for 2022, 11 Best ID Theft Protection Services for 2022 [Tested and Reviewed], 10 Best Parental Control Software for 2022, 10 Best VPN Services Tested And Measured in 2022, 7 Perfect VPN Services for the Dark Web in 2022, 10 Best Email Encryption Software for 2022, 10 Best Windows Server Backup Software for 2022, 10 Best Enterprise Backup Solutions for 2022, 10 Best Cloning Software for SSD for 2022, 9 Best Tenant Screening Services for 2022, 10 Best Background Check Services in 2022, 7 Best VPN Services For Torrenting for 2022, 11 Best Press Release Distribution Services for 2022, 13 Best Virtual Assistant Companies for 2022, 15 Best Video Streaming Services for 2022, 13 Best Online Learning Platforms for 2022, 7 Best Internet Options for Rural Areas for 2022, 26 Best Infographic Creation Tools for 2022, 15 Best Video Editing Software for Beginners in 2022, 10 Best YouTube to MP3 Converter for 2022, Best Transcription Software for 2022 - 10 Options Reviewed, The Best 9 Screenwriting Software You Can Get In 2022, The Best Drawing Software Artists Need in 2022, 12 Best Portable Monitor Options for 2022, 9 Best Motherboards for Ryzen 7 3700X for 2022, 8 Best Microphones for Streaming for 2022, 8 Best Dash Cam Models Under $100 for 2022, 12 Best Drawing Tablets for Beginners and Pros in 2022, 10 Best Shallow Mount Subwoofer Models for 2022, 7 Best External Hard Drives for Mac For 2022, 7 Best Bluetooth Speakers for Outdoor Party for 2022, Best Electric Garage Heaters 120V for 2022, 9 Best Cloud Gaming Service Providers for 2022, 9 Best Gaming Laptops Under 1000 for 2022, Best Generator for RV Air Conditioner for 2022, 55+ Jaw Dropping App Usage Statistics in 2022 [Infographic], 29 Important Blogging Statistics Every Blogger Should Know in 2022, 9 New Technology Trends That Will Shape Our Future, 27+ Biggest Data Breaches In History [Updated in 2022], What Is 3D Rendering? If a robbery took place and the perpetrators got away, how much of a head start do they have to cover their tracks? IoTs arent known for having excellent security. If you determine an endpoint is harmful, you can also take an aggressive containment move and lock down the endpoint, disabling its ability to communicate with any other endpoints. Prevent security breaches with endpoint detection and response.
endpoint endpoint ponemon security endpoint risk institute weaponisation data source state report Perhaps one of the most alarming cyber security statistics on this list is that 62% of global organizations cannot claim that they are equipped to handle a cyber attack. The numbers are estimated to increase over the years, reaching as high as $265 billion in 2031. Lets face itthreats against your business are on the rise and your board has zero tolerance for security issues. When a device is connected to your network, its considered an endpoint. One-third of small businesses in the UK and US use free, consumer-grade cybersecurity, and 23% dont use any endpoint security platform at all. What is Managed EDR Security?
security endpoint europe market report cagr 2024 marketersmedia sample request pdf surpass bn graphical research april Is it possible that cybercriminals have found new vulnerabilities? Read more, Could an Endpoint Security Service Be Your Secret Cybersecurity Weapon?. does pay. Spam filters: These tools can help to prevent unwanted email messages from reaching your inbox. Hospitals spend about $408 on every affected patient's record and $1.75 to fix their damaged reputation for every attack.
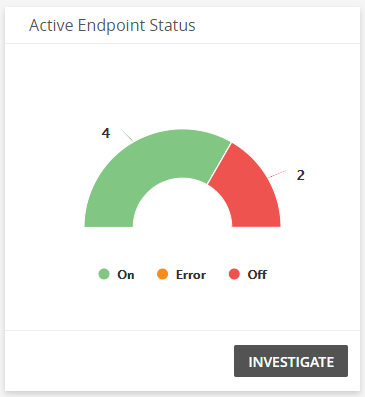

Recent research by SonicWall reported that recorded ransomware incidents last year represented a staggering 148% year-on-year increase over 2020.
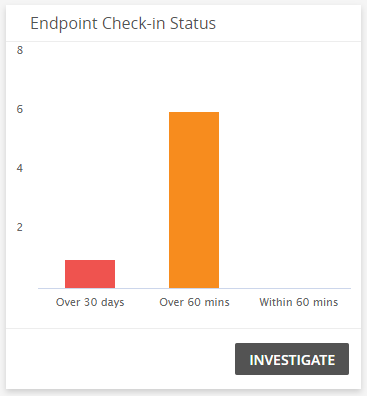
That represents a 400% increase from what they were seeing pre-coronavirus. These stats come from third-party surveys and reports, and well be updating them as new research emerges to help you stay on top of the latest figures. I believe most people are guilty of not changing their password often enough. The same study found that it takes an average of 97 days to apply, test and deploy a patch, and that 40% of organizations prefer to take their time in testing and rolling out patches in order to avoid issues later on. A portion of the rise is a result of the increased number of IoT devices, but the more significant issue is that related security isnt keeping pace with the growing number of threats.
uninstall endpoint 
The most important key figures provide you with a compact summary of the topic of "Endpoint security" and take you straight to the corresponding statistics.
 Once downloaded to the victims device, the malware holds corporate data hostage by locking users out of it or encrypting it until the target organization pays a ransom.
Once downloaded to the victims device, the malware holds corporate data hostage by locking users out of it or encrypting it until the target organization pays a ransom.  Smaller companies are more prone to cyber-attacks because they dont employ proper defenses against advanced cyber threats, contributing heavily to these cyber security statistics. Threat actors are creating malware like crazy. They can also help to prevent malicious software from infecting your devices. This, coupled with the projections for further data breaches, spells future challenges. Cyber attack statistics show this to be a key reason why harmful software for mobile devices is not such an issue anymore. These measures can include antivirus software, firewalls, and spam filters. By the end of 2021, there were, The Best Money Making Apps You'll Find in 2022 (Tested & Reviewed), 10 Best Appointment Scheduling Software for 2022, 11 Top CRM Software For Your Business for 2022, 10 Best Project Management Software for 2022, 10 Best Web Conferencing Software for 2022, 11 Best Membership Management Software for 2022, 9 Best Data Visualization Software for 2022, 10 Best Document Management Software For A Paperless Office for 2022, 12 Best Event Management Software for 2022, 11 Best Digital Signature Software for 2022, 10 Best Customer Experience Management Software for 2022, 10 Best Payment Gateway Providers for 2022, 20 Best Lead Generation Software For Marketers for 2022, 10 Best Reputation Management Software for 2022, 10 Top Contact Management Software for 2022, 14 Best Facebook Chatbots For Your Business Website for 2022, 10 Best Email Marketing Services for 2022, 9 Best Social Media Management Tools for 2022, 5 Leading Tax Software Solutions for 2022, 10 Best Online Bookkeeping Services for 2022, 10 Best Expense Management Software for 2022, 6 Best Web Hosting Companies In India for 2022, 9 Best WordPress Hosting Companies for 2022, 12 Best Privacy Policy Generators for 2022, 9 Best WordPress Security Plugins for 2022, 10 Best Minecraft Server Hosting Providers for 2022, 10 Best Shared Hosting Providers for 2022, 10 Best Cheap VPS Hosting Providers for 2022, 10 Best HR Software For Successful Business Leaders in 2022, 10 Best Employee Monitoring Software for 2022, 10 Best Employee Engagement Software for 2022, 10 Best Medical Billing Software for 2022, 10 Excellent Property Management Software for 2022, 16 Best Audio Recording Software for 2022, 11 Best Inventory Management Software for 2022, 10 Best Field Service Management Software for 2022, 10 Best Network Monitoring Software for 2022, 11 Best ID Theft Protection Services for 2022 [Tested and Reviewed], 10 Best Parental Control Software for 2022, 10 Best VPN Services Tested And Measured in 2022, 7 Perfect VPN Services for the Dark Web in 2022, 10 Best Email Encryption Software for 2022, 10 Best Windows Server Backup Software for 2022, 10 Best Enterprise Backup Solutions for 2022, 10 Best Cloning Software for SSD for 2022, 9 Best Tenant Screening Services for 2022, 10 Best Background Check Services in 2022, 7 Best VPN Services For Torrenting for 2022, 11 Best Press Release Distribution Services for 2022, 13 Best Virtual Assistant Companies for 2022, 15 Best Video Streaming Services for 2022, 13 Best Online Learning Platforms for 2022, 7 Best Internet Options for Rural Areas for 2022, 26 Best Infographic Creation Tools for 2022, 15 Best Video Editing Software for Beginners in 2022, 10 Best YouTube to MP3 Converter for 2022, Best Transcription Software for 2022 - 10 Options Reviewed, The Best 9 Screenwriting Software You Can Get In 2022, The Best Drawing Software Artists Need in 2022, 12 Best Portable Monitor Options for 2022, 9 Best Motherboards for Ryzen 7 3700X for 2022, 8 Best Microphones for Streaming for 2022, 8 Best Dash Cam Models Under $100 for 2022, 12 Best Drawing Tablets for Beginners and Pros in 2022, 10 Best Shallow Mount Subwoofer Models for 2022, 7 Best External Hard Drives for Mac For 2022, 7 Best Bluetooth Speakers for Outdoor Party for 2022, Best Electric Garage Heaters 120V for 2022, 9 Best Cloud Gaming Service Providers for 2022, 9 Best Gaming Laptops Under 1000 for 2022, Best Generator for RV Air Conditioner for 2022, 55+ Jaw Dropping App Usage Statistics in 2022 [Infographic], 29 Important Blogging Statistics Every Blogger Should Know in 2022, 9 New Technology Trends That Will Shape Our Future, 27+ Biggest Data Breaches In History [Updated in 2022], What Is 3D Rendering? If a robbery took place and the perpetrators got away, how much of a head start do they have to cover their tracks? IoTs arent known for having excellent security. If you determine an endpoint is harmful, you can also take an aggressive containment move and lock down the endpoint, disabling its ability to communicate with any other endpoints. Prevent security breaches with endpoint detection and response. endpoint endpoint ponemon security endpoint risk institute weaponisation data source state report Perhaps one of the most alarming cyber security statistics on this list is that 62% of global organizations cannot claim that they are equipped to handle a cyber attack. The numbers are estimated to increase over the years, reaching as high as $265 billion in 2031. Lets face itthreats against your business are on the rise and your board has zero tolerance for security issues. When a device is connected to your network, its considered an endpoint. One-third of small businesses in the UK and US use free, consumer-grade cybersecurity, and 23% dont use any endpoint security platform at all. What is Managed EDR Security? security endpoint europe market report cagr 2024 marketersmedia sample request pdf surpass bn graphical research april Is it possible that cybercriminals have found new vulnerabilities? Read more, Could an Endpoint Security Service Be Your Secret Cybersecurity Weapon?. does pay. Spam filters: These tools can help to prevent unwanted email messages from reaching your inbox. Hospitals spend about $408 on every affected patient's record and $1.75 to fix their damaged reputation for every attack.
Smaller companies are more prone to cyber-attacks because they dont employ proper defenses against advanced cyber threats, contributing heavily to these cyber security statistics. Threat actors are creating malware like crazy. They can also help to prevent malicious software from infecting your devices. This, coupled with the projections for further data breaches, spells future challenges. Cyber attack statistics show this to be a key reason why harmful software for mobile devices is not such an issue anymore. These measures can include antivirus software, firewalls, and spam filters. By the end of 2021, there were, The Best Money Making Apps You'll Find in 2022 (Tested & Reviewed), 10 Best Appointment Scheduling Software for 2022, 11 Top CRM Software For Your Business for 2022, 10 Best Project Management Software for 2022, 10 Best Web Conferencing Software for 2022, 11 Best Membership Management Software for 2022, 9 Best Data Visualization Software for 2022, 10 Best Document Management Software For A Paperless Office for 2022, 12 Best Event Management Software for 2022, 11 Best Digital Signature Software for 2022, 10 Best Customer Experience Management Software for 2022, 10 Best Payment Gateway Providers for 2022, 20 Best Lead Generation Software For Marketers for 2022, 10 Best Reputation Management Software for 2022, 10 Top Contact Management Software for 2022, 14 Best Facebook Chatbots For Your Business Website for 2022, 10 Best Email Marketing Services for 2022, 9 Best Social Media Management Tools for 2022, 5 Leading Tax Software Solutions for 2022, 10 Best Online Bookkeeping Services for 2022, 10 Best Expense Management Software for 2022, 6 Best Web Hosting Companies In India for 2022, 9 Best WordPress Hosting Companies for 2022, 12 Best Privacy Policy Generators for 2022, 9 Best WordPress Security Plugins for 2022, 10 Best Minecraft Server Hosting Providers for 2022, 10 Best Shared Hosting Providers for 2022, 10 Best Cheap VPS Hosting Providers for 2022, 10 Best HR Software For Successful Business Leaders in 2022, 10 Best Employee Monitoring Software for 2022, 10 Best Employee Engagement Software for 2022, 10 Best Medical Billing Software for 2022, 10 Excellent Property Management Software for 2022, 16 Best Audio Recording Software for 2022, 11 Best Inventory Management Software for 2022, 10 Best Field Service Management Software for 2022, 10 Best Network Monitoring Software for 2022, 11 Best ID Theft Protection Services for 2022 [Tested and Reviewed], 10 Best Parental Control Software for 2022, 10 Best VPN Services Tested And Measured in 2022, 7 Perfect VPN Services for the Dark Web in 2022, 10 Best Email Encryption Software for 2022, 10 Best Windows Server Backup Software for 2022, 10 Best Enterprise Backup Solutions for 2022, 10 Best Cloning Software for SSD for 2022, 9 Best Tenant Screening Services for 2022, 10 Best Background Check Services in 2022, 7 Best VPN Services For Torrenting for 2022, 11 Best Press Release Distribution Services for 2022, 13 Best Virtual Assistant Companies for 2022, 15 Best Video Streaming Services for 2022, 13 Best Online Learning Platforms for 2022, 7 Best Internet Options for Rural Areas for 2022, 26 Best Infographic Creation Tools for 2022, 15 Best Video Editing Software for Beginners in 2022, 10 Best YouTube to MP3 Converter for 2022, Best Transcription Software for 2022 - 10 Options Reviewed, The Best 9 Screenwriting Software You Can Get In 2022, The Best Drawing Software Artists Need in 2022, 12 Best Portable Monitor Options for 2022, 9 Best Motherboards for Ryzen 7 3700X for 2022, 8 Best Microphones for Streaming for 2022, 8 Best Dash Cam Models Under $100 for 2022, 12 Best Drawing Tablets for Beginners and Pros in 2022, 10 Best Shallow Mount Subwoofer Models for 2022, 7 Best External Hard Drives for Mac For 2022, 7 Best Bluetooth Speakers for Outdoor Party for 2022, Best Electric Garage Heaters 120V for 2022, 9 Best Cloud Gaming Service Providers for 2022, 9 Best Gaming Laptops Under 1000 for 2022, Best Generator for RV Air Conditioner for 2022, 55+ Jaw Dropping App Usage Statistics in 2022 [Infographic], 29 Important Blogging Statistics Every Blogger Should Know in 2022, 9 New Technology Trends That Will Shape Our Future, 27+ Biggest Data Breaches In History [Updated in 2022], What Is 3D Rendering? If a robbery took place and the perpetrators got away, how much of a head start do they have to cover their tracks? IoTs arent known for having excellent security. If you determine an endpoint is harmful, you can also take an aggressive containment move and lock down the endpoint, disabling its ability to communicate with any other endpoints. Prevent security breaches with endpoint detection and response. endpoint endpoint ponemon security endpoint risk institute weaponisation data source state report Perhaps one of the most alarming cyber security statistics on this list is that 62% of global organizations cannot claim that they are equipped to handle a cyber attack. The numbers are estimated to increase over the years, reaching as high as $265 billion in 2031. Lets face itthreats against your business are on the rise and your board has zero tolerance for security issues. When a device is connected to your network, its considered an endpoint. One-third of small businesses in the UK and US use free, consumer-grade cybersecurity, and 23% dont use any endpoint security platform at all. What is Managed EDR Security? security endpoint europe market report cagr 2024 marketersmedia sample request pdf surpass bn graphical research april Is it possible that cybercriminals have found new vulnerabilities? Read more, Could an Endpoint Security Service Be Your Secret Cybersecurity Weapon?. does pay. Spam filters: These tools can help to prevent unwanted email messages from reaching your inbox. Hospitals spend about $408 on every affected patient's record and $1.75 to fix their damaged reputation for every attack. 
 Recent research by SonicWall reported that recorded ransomware incidents last year represented a staggering 148% year-on-year increase over 2020.
Recent research by SonicWall reported that recorded ransomware incidents last year represented a staggering 148% year-on-year increase over 2020.  That represents a 400% increase from what they were seeing pre-coronavirus. These stats come from third-party surveys and reports, and well be updating them as new research emerges to help you stay on top of the latest figures. I believe most people are guilty of not changing their password often enough. The same study found that it takes an average of 97 days to apply, test and deploy a patch, and that 40% of organizations prefer to take their time in testing and rolling out patches in order to avoid issues later on. A portion of the rise is a result of the increased number of IoT devices, but the more significant issue is that related security isnt keeping pace with the growing number of threats. uninstall endpoint
That represents a 400% increase from what they were seeing pre-coronavirus. These stats come from third-party surveys and reports, and well be updating them as new research emerges to help you stay on top of the latest figures. I believe most people are guilty of not changing their password often enough. The same study found that it takes an average of 97 days to apply, test and deploy a patch, and that 40% of organizations prefer to take their time in testing and rolling out patches in order to avoid issues later on. A portion of the rise is a result of the increased number of IoT devices, but the more significant issue is that related security isnt keeping pace with the growing number of threats. uninstall endpoint  The most important key figures provide you with a compact summary of the topic of "Endpoint security" and take you straight to the corresponding statistics.
The most important key figures provide you with a compact summary of the topic of "Endpoint security" and take you straight to the corresponding statistics.